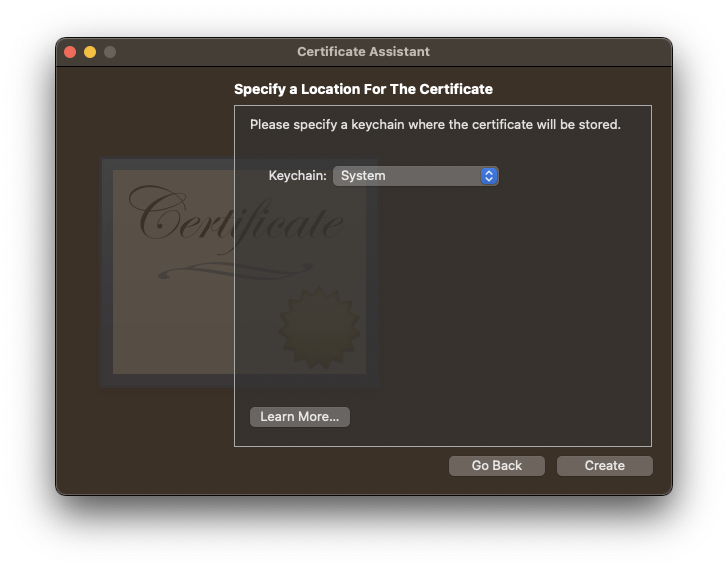
6. Enter your login credentials when prompted and press `Done`
### Signing of G-Mem
1. Open `Terminal` (press `⌘ + Enter`, type `Terminal` to open it from spotlight)
2. Type `codesign -fs "gmem-cert" ` (do not press enter yet)
3. Drag the `G-Mem` file into your terminal window (this will append the path to the file)
Your terminal window should now resemble the following:
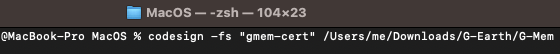
4. Now press enter and enter your login credentials when prompted.
### Making G-Mem executable
1. Open `Terminal` (press `⌘ + Enter`, type `Terminal` to open it from spotlight)
2. Type `chmod 755 ` (do not press enter yet)
3. Drag the `G-Mem` file into your terminal window (this will append the path to the file)
Your terminal window should now resemble the following:
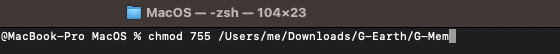
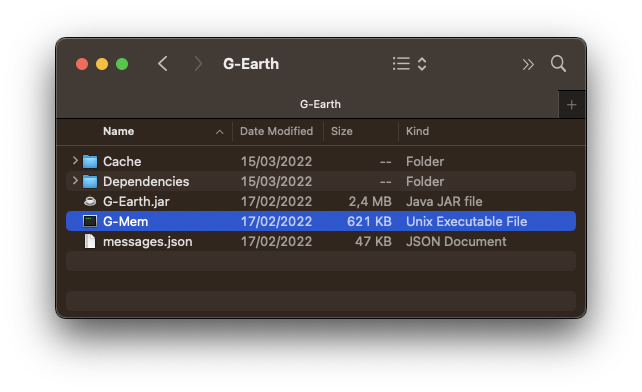
4. Now press enter and verify the `Kind` of the `G-Mem` file is not `Unix Executable File`
## Disabling SIP
Modern machines running MacOS have a security feature that shields of the memory of processes from other processes.
Depending on your machine you may have to disable SIP.
**For M1 macs it is required to disable SIP.**
### :warning: CAUTION :warning:
Turning off SIP allows any program with sudo privileges to modify memory contents of other processes. If you use pirated software, or other unverified apps, DO NOT DO THIS for your own safety! See the following stackoverflow post for some more info: https://apple.stackexchange.com/a/412281.